Why We Filed a Patent for Our Technology
Digital documents are often legally relevant today – for example, in accounting, business transactions, or internal documentation. But how can you reliably prove that a file existed at a specific time, remained unchanged – or when it was modified?
Our Technology: Why We Filed a Patent Application
With our patent application, we describe a technical solution to a very specific problem: an economically efficient, tamper-proof, and independently verifiable audit-proof archiving method for entire directory trees – not just individual files.
In this blog post, we provide an overview of our invention, how it works, and the practical benefits for users.
The full patent application is available here.
1. What Audit-Proof Archiving Means
A storage system is considered audit-proof if it can reliably prove that:
- a specific file existed at a specific point in time – and was not backdated later,
- an entire directory with all its contents existed at a specific point in time,
- all changes and deletions are documented and traceable,
- nothing has been removed from the historical record – for example, the existence of a past file cannot be deleted retroactively.
These requirements are especially relevant for GoBD-compliant archiving under German tax law.
2. What Existing Solutions Fail to Deliver
There are several established technologies for securing digital data – but they each have clear limitations:
- Digital signatures with timestamps (e.g. RFC 3161): These only work for individual files. To archive directories, users must create ZIP archives and sign them, which quickly leads to excessive storage usage.
- OpenTimestamps: Secures hashes via the Bitcoin blockchain using Merkle trees. Users must store the proof files themselves. For directories, the same drawbacks apply as with digital signatures.
- Content Addressed Storage (e.g. Git): Uses hash-based versioning but lacks independent timestamps. Furthermore, Git relies on the outdated and insecure SHA-1 hash algorithm.
- Direct blockchain storage: Very expensive, not scalable, and publicly visible – making it unsuitable for confidential or large volumes of data.
What’s missing is a scalable, efficient, and audit-proof solution for complete directory structures – with a verifiable history and independently checkable timestamps.
3. The Goal and Problem Our Invention Solves
Our invention is designed to close exactly this gap – with a system that:
- enables audit-proof archiving of entire directory structures,
- remains cost-efficient even with large volumes of data,
- works without relying on any trusted central party,
- and allows for the verification of individual files or folders – without having to reveal the entire archive.
4. Our Solution: CAS, Merkle Trees, and Blockchain
Our technology combines three proven concepts into a novel, highly scalable architecture: Content Addressed Storage (CAS), Merkle trees, and blockchain-based timestamping.
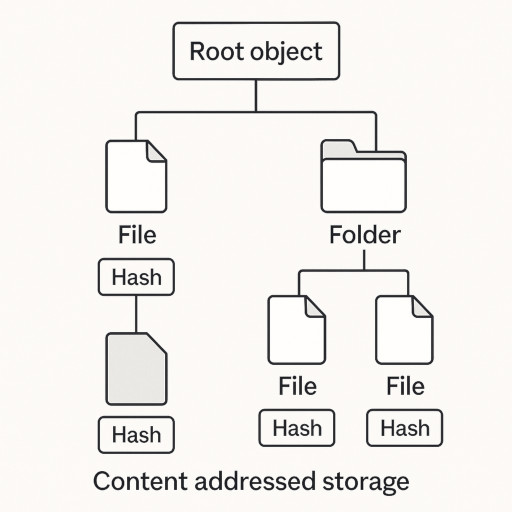
In the first step, files and folders are stored as so-called objects. Their address is derived directly from their content – specifically from a cryptographic hash. Any content change automatically creates a new object with a new hash. Linking these objects creates a tree structure with a so-called root object at the top. This root object represents the complete state of the entire data space at a specific point in time.
Changes in the file system generate what we call commits. Each new commit references the previous root object, creating a complete historical chain. Additionally, files or directories reference their predecessor objects where applicable. This builds a technically verifiable, chronological change history – without the need to analyze complex logs or diff files. At any time, it’s possible to reconstruct exactly when a file was created, modified, or deleted.
To make this structure audit-proof, the hash of the current root object is written to a public blockchain at regular intervals – typically once per day at midnight. We use Ethereum (via Arbitrum) for this purpose. Only the hash is stored, never the actual content. This ensures full GDPR compliance and protects user privacy.
This regular anchoring creates a verifiable timeline. For example, one could prove that a file was created between February 21st and 22nd – and definitely did not exist before that. Retroactive manipulation would only be possible if all subsequent objects and blockchain entries were deleted or falsified at once – which is virtually impossible.
To increase efficiency, multiple hashes can be bundled into a Merkle tree. Only the top hash of the tree needs to be anchored. Individual objects can later be proven independently using a Merkle proof – without revealing any unrelated content.
Selective verification is also possible: individual files or entire folders can be exported and proven as audit-compliant. The hash of the object combined with its Merkle proof is sufficient. To support selective deletion and data protection, content such as filenames or plaintext data is stored separately in encrypted content objects. This allows for partial deletion without compromising the integrity of the entire archive.
5. Real-World Use Cases
Example 1: GoBD-Compliant Archiving
Receipts, contracts, or proposals are stored in such a way that they can no longer be altered or deleted without detection – ideal for tax-related compliance.
Example 2: Shareholder Resolutions
All protocols remain traceable and tamper-proof – even if only one managing director has access. Deleting individual resolutions retroactively is impossible.
This is especially important during audits or financial reviews, where documented decisions often carry legal or tax relevance.
Example 3: Due Diligence Processes
In company sales or mergers, it’s essential that all relevant documents are available in an audit-proof manner.
Sellers and buyers can securely and permanently prove what was made available when – independently of any third-party service provider.
6. How Versiobit Implements This Today
Versiobit already implements this technology in practice, offering a cloud-based, audit-proof storage solution for files and directories. Our users benefit from:
- ✅ Audit-proof storage based on the described invention
- ✅ End-to-end encryption for maximum data privacy
- ✅ Cross-device synchronization to always work with the latest data
- ✅ Daily history compaction to reduce unnecessary storage usage
- ✅ Exportable proofs for individual file versions or folders, for audits or official documentation
7. Conclusion
With this technology, Versiobit combines the efficiency of modern versioning systems with the immutability of public blockchains.
The result is an audit-proof storage solution that is independent, verifiable, and cost-efficient – and that works reliably in the long term, even without a central instance.
To learn more, see the official patent application.